

Blogs 
January 30, 2018
Living Security Team
Strava: A Curious Case for Security Awareness
Strava: A Curious Case for Security Awareness
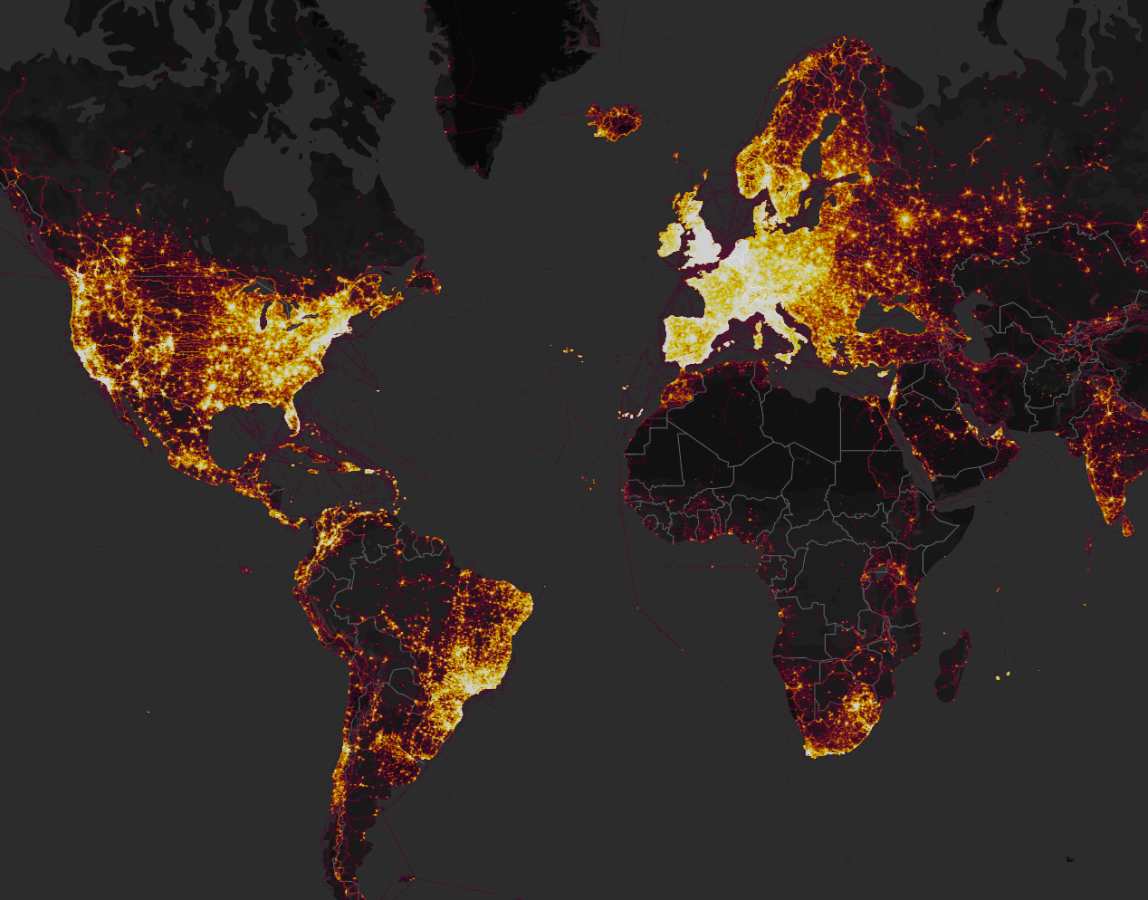
The Strava Fitness app is marketed as a tool that “connects the world’s athletes.” Meaning, it’s an application for most phones and GPS-enabled watches that hosts fitness clubs and triathletes, gym rats and track stars, sweat-junkies and granola types – all in one platform. The power of Strava is in its ability to collect enough information to fulfill any New Years Resolution. The downside is that it also manages to publicize location, contact information and fitness activities on a heat-map, amounting to some “three trillion GPS data points” worldwide.
One researcher recently discovered, for example, that members of the armed forces were unintentionally mapping global military infrastructure as they jogged or biked with Strava. This is a classic case of data privacy loss: sensitive information disclosed to unauthorized parties inadvertently. Strava did not intend for these data points to uncover sensitive military outposts, of course. But consent is a fickle friend. Once the risk was ‘franchised’ to Strava, the unintentional disclosure was outside of military control.
From a user perspective, this brings many different forces to bear: users feel like they have limited control of their privacy, passive control of their consent and little reason to change. Privacy settings in most applications typically default public, risk declarations are in fine print and data just feeds the beast, right?
If users are made aware of the implications of their data-made-public, they are far more likely to take advantage of the control they do have over their privacy and exert it in a way that matters. Practically, this looks like changing default settings to private, opting out of inappropriate data gathering and employing the ultimate failsafe (if privacy disrespected): app removal. In the workplace, this means waging culture change by way of powerful awareness activities that communicate to employees in language and methods they can intuitively understand.
This Strava scenario could live and die as a classic case of data privacy loss. Or it could teach us something… that even curious cases like a map of the global military-fitness complex is a reason to reclaim privacy now.
Living Security is a company committed to throwing out the security soapbox and taking a fresh approach to security awareness.
Our Mission
At Living Security, we reduce the #1 cybersecurity risk for enterprises, human error, through engaging and impactful security awareness training that is brought to life by innovative tech enabled experiences.
Living Security co-founders, Ashley and Drew Rose, recognized that traditional security awareness programs were failing to move the needle and it was time for a fresh approach. Our immersive training experiences engage the enterprise using science backed techniques to motivate behavior change and refreshed content that’s relevant for the current threat landscape.
Immersive Cyber Escape Room
Our innovative Cybersecurity Escape Room experience builds security awareness concepts into an engaging team experience people actually enjoy. Watch the video here.
Customized Cybersecurity Training At Scale
Online security awareness training platform leverages game based learning and a custom curriculum to make cybersecurity awareness training fun and effective.
Hosted Platform or SCORM Delivery
Our gamified training platform allows program owners to assign users training and track through completion and beyond. Our interactive video series are broken in to episodes that cover critical security awareness concepts through story based learning and interactive puzzles. Customize your program through the addition of role and concept specific micro-modules and incentivize completion through leaderboard challenges and rewards and recognition. Series and modules are also available in your SCORM packages for delivery on your LMS.