.png)
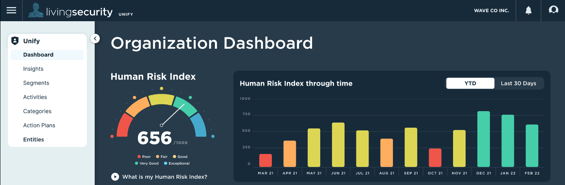
For a limited time, we're offering qualified organizations a free proof of value using your own data from your existing cybersecurity technologies.
✔ Extend security visibility from data & devices to employees
✔ Speed time to mitigation with targeted behavior & policy action plans
✔ Shrink your attack surface by reducing insider threats
Use event data from all of your existing security tools—Mimecast, Proofpoint, Zscaler, Okta, CrowdStrike (and many others)—and correlate it at the user level to see your riskiest locations, departments, and job roles.

Human Risk Management Operations Center (HROC)?Unify, Living Security's Human Risk Management platform, introduces the HROC. It's one pane of glass that identifies your riskiest individuals, helps you efficiently plan next actions, and measures the impact of improving human behavior.
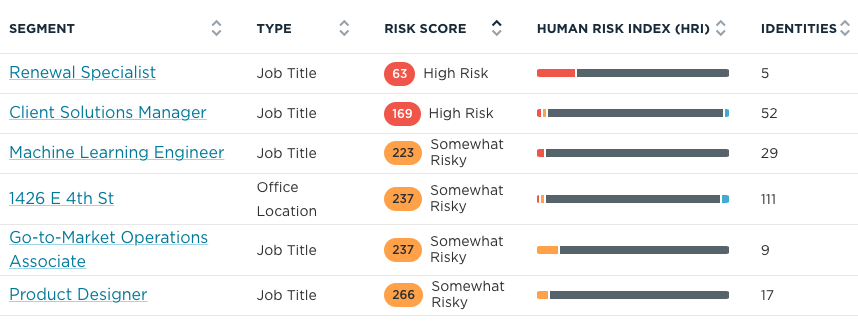
When you can identify your riskiest employees—by title, location, department, or individually—you gain the power to confidently improve your organization's risk profile.
Why do certain teams or locations exhibit higher risks? Asking this question spurs business conversations with leaders and empowers collaborative problem-solving.
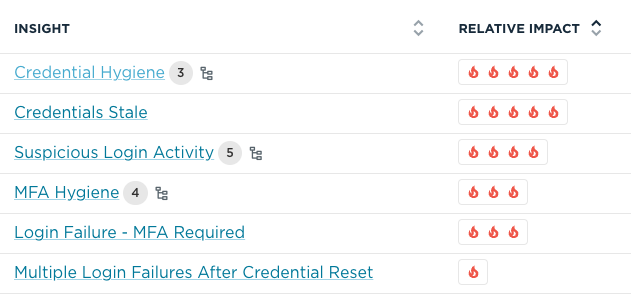
Whatever insights are most important to you, Unify's HROC not only shows you the category of risk, but also the relevant impact of solving it. You can even see what your Human Risk Index will be once the issue is resolved.
The human behavior context helps you prioritize your next actions to improve your cybersecurity posture. What's more, you'll easily progress right here in the HROC.
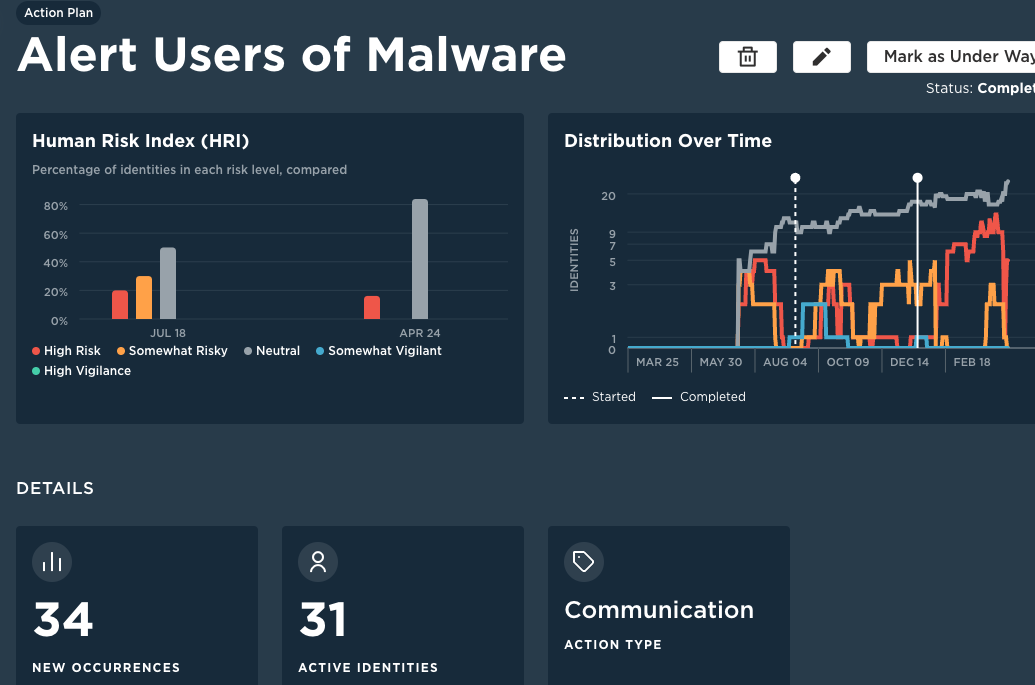
Today, you may be waiting until something bad happens because you don't know where to focus your team's efforts. With Unify, Human Risk Management, and the HROC, the answer is right in front of you.
Finally stop pulling manual reports from your expensive, disconnected cybersecurity technologies and tools. Your HROC integrates with your existing data to bring it to life so you can know everything and do anything.
Your new HROC shows you data from your existing tools in context of human behaviors within your organization. No more guesswork. You'll know exactly where and who your human risks are, and what do to next.

KnowBe4
Phishing & Email, Training Compliance, Account Compromise, Malware
What Is Human Risk Management?Organizations spend billions on cybersecurity technology, yet 80% of security breaches result from human actions. Human risk management looks at how your users take risks every day, highlighting the riskiest employees. This data comes from the technologies you already own, then shows it to you at a person, team, or role level.
When you see your riskiest users, you can take swift action—more training, new policies—and make the biggest impact on security by focusing on these users and ignoring more vigilant ones.
It's a proactive approach that helps you take the most efficient steps to improve your security posture. Unify by Living Security leads the industry in human risk management. Here's how it works.
For the first time, see data from all your cybersecurity technologies correlated to individuals, teams, locations, and roles. No wrangling reports from various tools. Get more value from your technology investments.
On one pane of glass, Unify shows you which employees are taking risks with data. Is the Accounting team clicking on phishing emails? Is the Cleveland office "working around" their MFA? These insights fuel conversations that drive understanding and next actions.
Armed with the view of the exact employees taking specific risks, you can pinpoint policy changes or deploy additional training directly to those who need it. Prioritizing your riskiest users makes the biggest, fastest impact on your security posture.
Unify shows you risky behaviors, prioritizes next actions, and shows you the impact of the changes—all on one pane of glass. You can report results directly from Unify without spending hours manually collating data from each of your cybersecurity tools.
Clients











