.png)
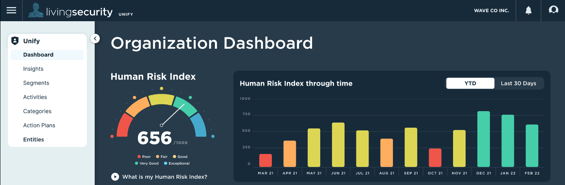
Living Security is enabling Unify Go for all of our Training Platform clients. This will unlock human risk management tools including trend analysis around actions taken to mitigate those risks.
Unify Go is limited to identifying Social Engineering risks. This requires three integrations:
✔ Email Security Tool: Identifies who is targeted by actual phishing attempts and identifies who is reporting real and suspect phishing attempts
✔ Phishing Simulation Tool: Gages phish identification and reporting acumen in a safe environment
✔ Training Platform: Enrolls identified individuals into training based on their behaviors and engagement with training content.

The Unify Go dashboard shows you data from your existing tools in context of human behaviors within your organization. No more guesswork. You'll know exactly where and who your human risks are, and what do to next.

KnowBe4
Phishing & Email, Training Compliance, Account Compromise, Malware

OKTA
Customer Identity Management

Sailpoint
Customer Identity Management
What Is Human Risk Management?Organizations spend billions on cybersecurity technology, yet 80% of security breaches result from human actions. Human risk management looks at how your users take risks every day, highlighting the riskiest employees. This data comes from the technologies you already own, then shows it to you at a person, team, or role level.
When you see your riskiest users, you can take swift action—more training, new policies—and make the biggest impact on security by focusing on these users and ignoring more vigilant ones.
It's a proactive approach that helps you take the most efficient steps to improve your security posture. Unify by Living Security leads the industry in human risk management. Here's how it works.
For the first time, see data from all your cybersecurity technologies correlated to individuals, teams, locations, and roles. No wrangling reports from various tools. Get more value from your technology investments.
On one pane of glass, Unify shows you which employees are taking risks with data. Is the Accounting team clicking on phishing emails? Is the Cleveland office "working around" their MFA? These insights fuel conversations that drive understanding and next actions.
Armed with the view of the exact employees taking specific risks, you can pinpoint policy changes or deploy additional training directly to those who need it. Prioritizing your riskiest users makes the biggest, fastest impact on your security posture.
Unify shows you risky behaviors, prioritizes next actions, and shows you the impact of the changes—all on one pane of glass. You can report results directly from Unify without spending hours manually collating data from each of your cybersecurity tools.
Clients











