

Products 
Security Awareness Training
Build a Security-Conscious Culture with Interactive Training for Modern Threats
Protect your team from evolving cyber dangers with scalable, flexible training that delivers engaging, immersive content wherever your employees are.
Test Drive Training
Engage employees with immersive and tailored cybersecurity training that wildly changes behaviors.
Leverage hundreds of professionally produced plot-driven, live-action, and captivating content modules to train employees on their specific and individualized risks and meet compliance requirements. Living Security’s Unify platform, illuminates areas of risk, empowering you to deploy training to those that need it most, extending the value and impact of your security training content. This tailored approach fosters deeper engagement and knowledge retention, equipping your employees with the skills to effectively identify and mitigate security risks while rewarding your vigilant users with time back in their day.


-thumb-1.jpeg)



What is Security Awareness Training?
Security awareness training is a strategy used by companies to mitigate risks by educating employees about good practices and common online “traps” set by cyber criminals. Living Security's Unify solution helps companies target and train their riskiest employees, improving security while rewarding the vigilant.Here’s How Living Security Helps You Reduce Human-Led Risk.

Tailored Learning
Assign targeted training based on roles, industries, and specific risk areas. Eliminate wasted time with irrelevant training and empower your workforce with actionable knowledge.

Launch in Minutes
Get security training campaigns up in running in record time with ready-to-use templates in more than 26 languages with pre-defined audience filters based on roles and departments, along with ability to manage multiple campaigns at a time.

Boost Engagement
Living Security training has over 100,000 5-star user reviews. Simplify learning and drive behavior change with contextual reminders and nudges delivered through your preferred communication tools. Training is accessible and personalized with 26 languages available for a global workforce.
Why Many Security Awareness Programs Fail
Organizations mandate annual check-the-box compliance training, but it does little to change human behavior.
Most security awareness training consists of a single one-size-fits-all component. Problem is, every organization has different types of workers, and individuals play roles that may increase their ability to impact security. Industry- and role-based training provides relevant experiences, aiding retention.
Usually, the IT Security Manager mandates once-a-year compliance training, with a goal to “check the box” rather than “enable employees to secure company data and assets.” This short-sighted approach can have a major negative impact on the organization if an employee causes a breach.
With completion-only goals, organizations lose the real value of training: measuring the impact on the organization as a whole. Did behavior change? Is the company more secure? Most training platforms cannot provide these deeper metrics and, therefore, never realize the full benefits of cybersecurity awareness training.
One-size-fits-all annual compliance training impedes productivity because it trains vigilant users the same as uneducated ones. Such training takes hours, is boring because it’s not relevant to the user, and feels mandated, so it’s no wonder employees don’t take it seriously, opting to just “get through” the training.
Adaptive Security Awareness Should Be a Part of Your Framework
At Living Security, all our security awareness and training programs aim to change behavior and empower all employees to defend against risks, making them powerful assets in keeping your organization’s data secure.
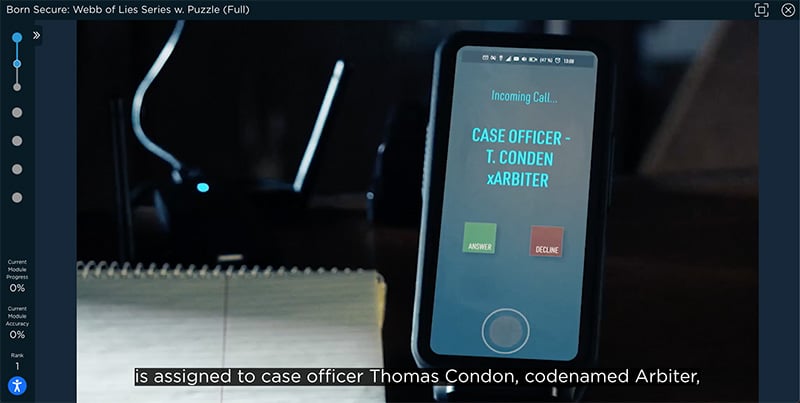
- Living Security delivers training that immerses employees in a story, so it’s more likely to be remembered.
- High-quality, well-acted videos convey key points as memorable plot points.
- Quick vignettes and puzzles that quiz employees, then build on their knowledge.
.jpg)
- Train for risks that are specific to employees with special access or privileges based on their roles.
- Risks for those in marketing differ than those in manufacturing; Living Security offers department-based training.
- Deploy specific training to teams or employees demonstrating risky behavior without burdening vigilant employees.
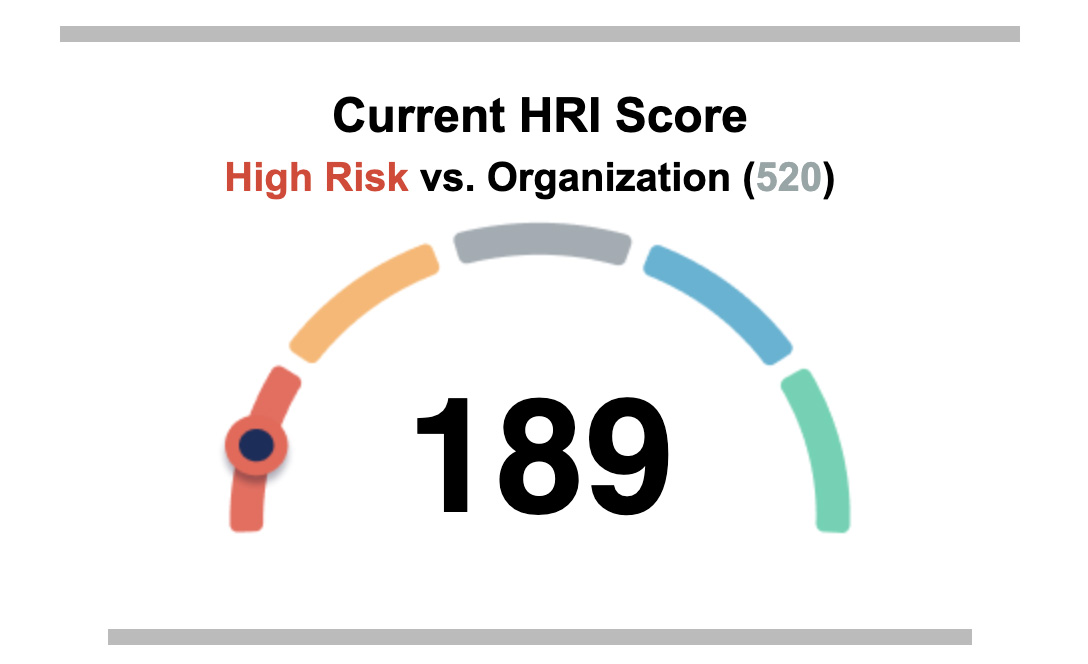
- With Human Risk Management, report on improvements in individual, team, and company-level risk mitigation.
- Illustrate areas of risk to deploy risk- or role-based training.
- Finally quantify your cybersecurity investment and its correlation to your organization’s ability to mitigate risk.
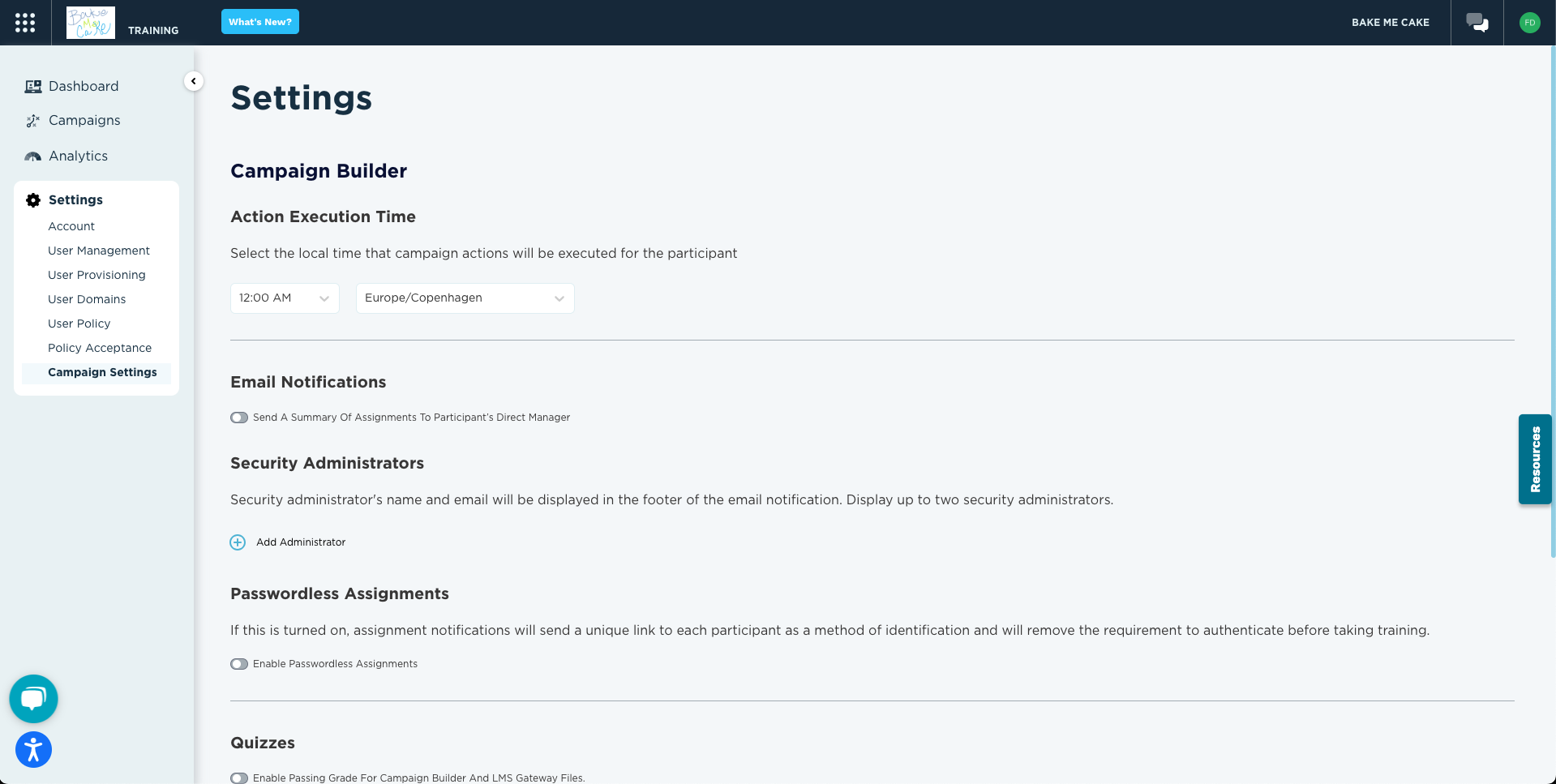
- Intuitive platform provides easy deployment of training to specific subsets to improve efficiencies.
- Discover, stage, and distribute ongoing awareness content in one easy platform.
- Ready-to-use content to easily reinforce security awareness throughout the year.


Living Security’s wide array of educational (and fun!!) content has improved our cyber education program tenfold. The escape room is one of our program’s highlights, and each month we typically host 5-10 escape room sessions for our colleagues and they absolutely love the experience.
Liz Jones, Senior Associate of Information Security & Response
Learn more about Human Risk Management
View All Resources
Feature
Human Risk Management Conference 2024
Human Risk Management conference brings together cybersecurity professionals to discuss improving human risk management and cybersecurity risk management.
Learn Why Organizations Choose Living Security
Fortune 500 companies trust Living Security to deliver human risk management by using existing data to identify risky employees or teams and target immersive training to those who need it most. This approach keeps organizations ahead of breaches and enables them to track their progress toward a better security posture. This proactive, automated, efficient approach saves resources while keeping employees and data safe.
Schedule a meeting today and let's get started.

