

PLATFORM 
 360 Degree Human Risk Visibility
360 Degree Human Risk Visibility
See What Your
Security Stack Misses
Uncover the riskiest users, behaviors, and blind spots across your organization—before attackers do.
AI- Recommendation Engine
Our innovative human risk Recommendations feature in the Unify platform- available for select customers- addresses the critical challenge that many organizations face, struggling to make sense of the vast amount of human risk data generated by their cybersecurity tools. By leveraging the power of AI, the Unify can now quickly analyze over 200 risky and vigilant behaviors, surfacing the most relevant risk data and correlating events in a matter of minutes. Recommendations identifies top risks and recommends interventions, assisting security leaders in taking immediate action through targeted interventions based on idustry-proven best practices, all within a few clicks.
“With Recommendations, we’ve streamlined the process and are the first to offer a solution that not only identifies change in human risk across the business but also prescribes the next best steps for mitigating that risk. This allows security teams to focus on what matters most – protecting their organization.”
- Kelly Harward | VP of Product, Living Security
 Significantly Reduce Exposure to Vulnerabilities
Significantly Reduce Exposure to Vulnerabilities
 Eliminate the Guesswork
Eliminate the Guesswork
Recommendations and its AI-tailored intelligence, eliminates the guesswork involved in identifying, prioritizing, and addressing human behavior that pose the greatest risk to business operations.
 Follow Actionable Playbooks
Follow Actionable Playbooks
Each AI-powered Recommendation is paired with an actionable playbook to mitigate identified risks through targeted training, behavioral nudges, automated workflows, or policy changes, enabling security programs to address human-initiated risks.
 Key Business Outcomes
Key Business Outcomes
- Faster identification of high-risk user groups
- Targeted, automated interventions to mitigate specific risks
- Prioritize actions based on estimated impact and ROI to operations
- Increased efficiency for security teams, saving time and reducing manual effort
- Actionable insights specific to key cohorts, driving faster risk reduction
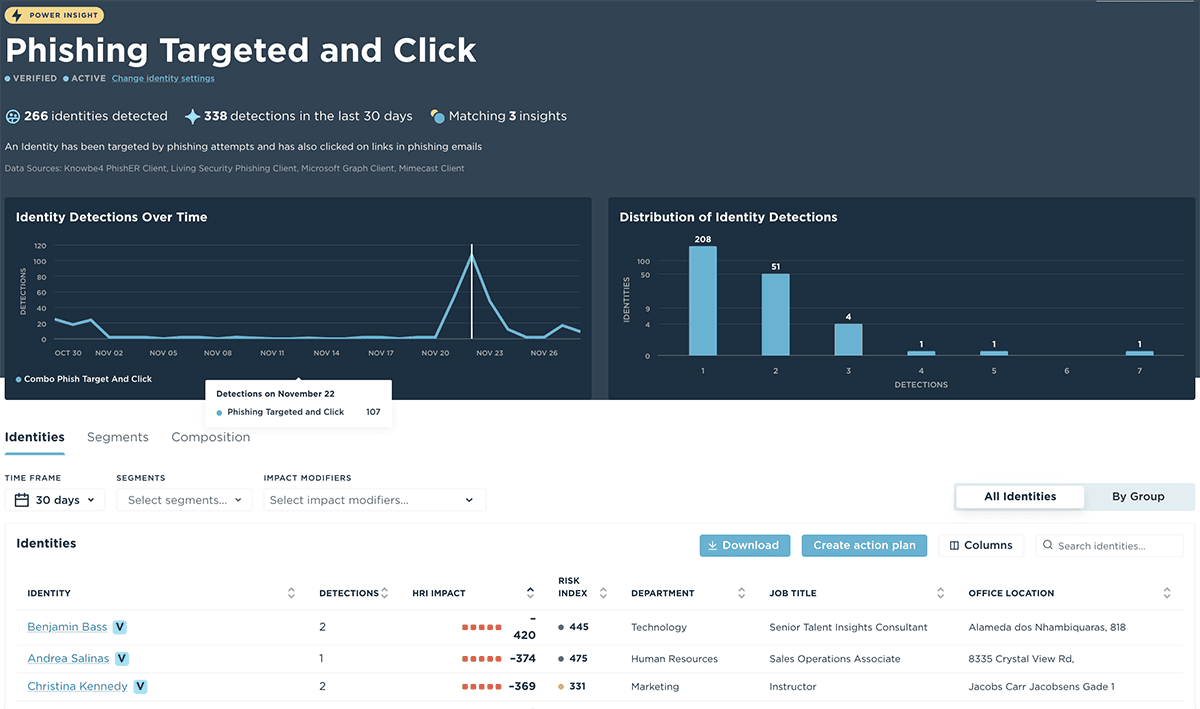
Identify Cyber Risks Your Employees Face
Discover your riskiest and most vigilent employees by title, location, or department. Gain the power to confidently improve your organization's risk profile. By integrating with your existing cybersecurity technology, Unify HROC gives you a single pane of glass to help you understand — and act on — the activities of your riskiest individuals, helping you efficiently plan next actions and measure the impact of improving human behavior.
Human Risk Quantification
Gain transparency with Human Risk Index (HRI) scores based on hundreds of tracked behaviors to understand where human risk is in your organization without guesswork or manual calculations.
The HRI score is a proprietary, patent-pending algorithm that incorporates hundreds of data points from an organization’s existing technology platforms. Each HRI score takes into account risky and vigilant behaviors, external threats, and an individual’s identity and access as context to determine if specific behaviors are more or less risky.
For example, some activities might be weighted as more risky for individuals with privileged access based on their role as compared to similar activities from someone with less access.
By automatically aggregating and correlating data across existing systems, the HRI algorithm efficiently and accurately distills complex behavior patterns into organizational, segment, and individual Human Risk Index scores.
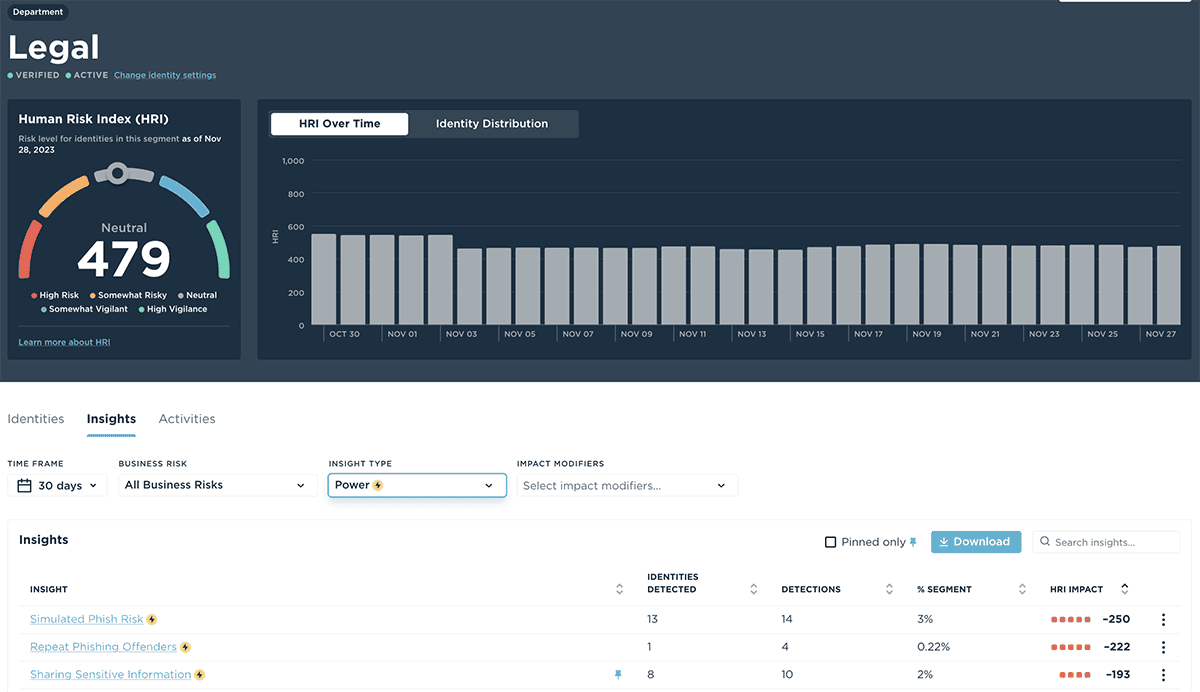
What's Your Biggest Human Risk?
Supercharge the Unify Human Risk Operations Center by empowering security teams to go beyond tracking individual device and data events. Instead Unify correlates a variety of behaviors and events from dozens of security tools to individual members of the workforce.
Track crucial groupings of user behaviors by combining insights across security tools to pinpoint risky users such as those who fail phishing simulations and are actively targeted by real phishing.
Correlate risky behaviors with external risk by seeing when a correlated collection of behaviors coupled with external threats puts your organization at heightened risk of social engineering, phishing, identity threats, data loss, malware, and more.
Shrink the internal attack surfaces by deploying action plans that include behavioral nudges, training, phishing, or policy changes to shift high-risk members of the workforce to vigilant influencers.
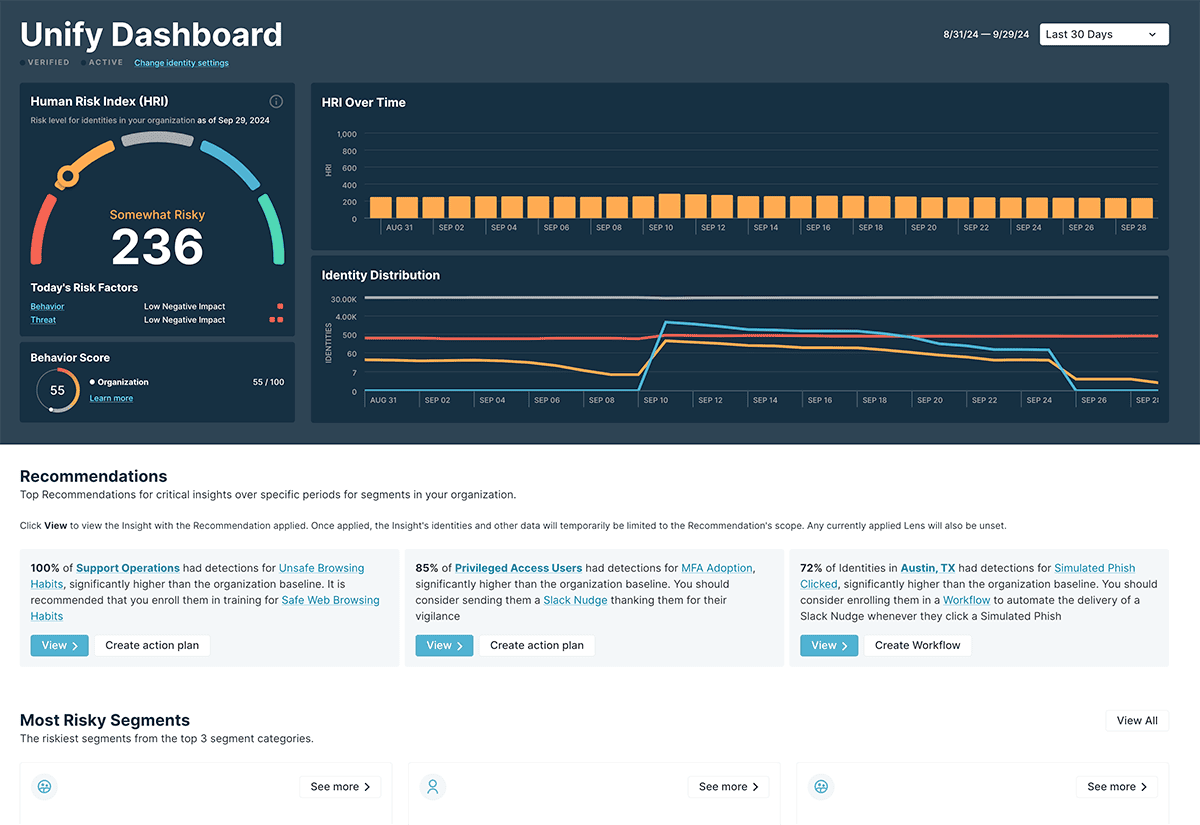
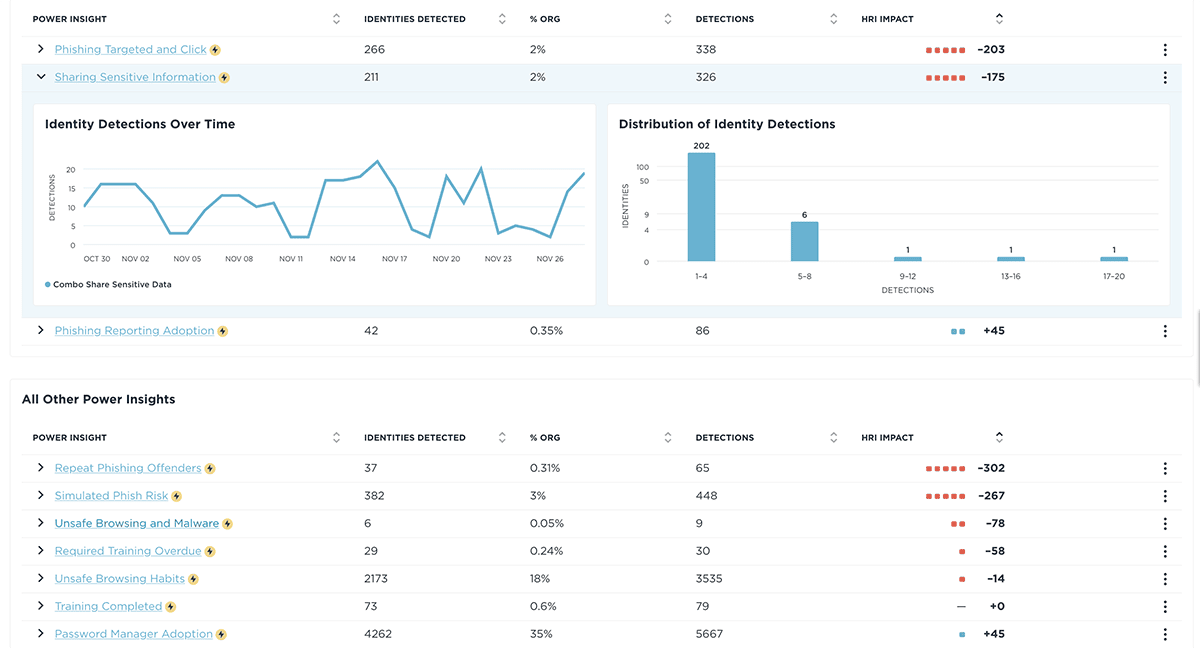
Supercharge AI Recommendations
Leverage the power of AI to automatically analyze over 250 risky and vigilant behaviors, surfacing the most relevant risk data and correlating events in a matter of minutes. Eliminate the guesswork involved in identifying, prioritizing, and addressing human behaviors that pose the greatest risk to business operations.
Unify's AI-based Recommendations supercharges your ability to identify top risks and recommends appropriate interventions, assisting security leaders in taking immediate action through targeted interventions based on industry-proven best practices, all within a few clicks. Identify high-risk user groups faster than ever, and prioritize actions based on estimated impact and ROI to operations.
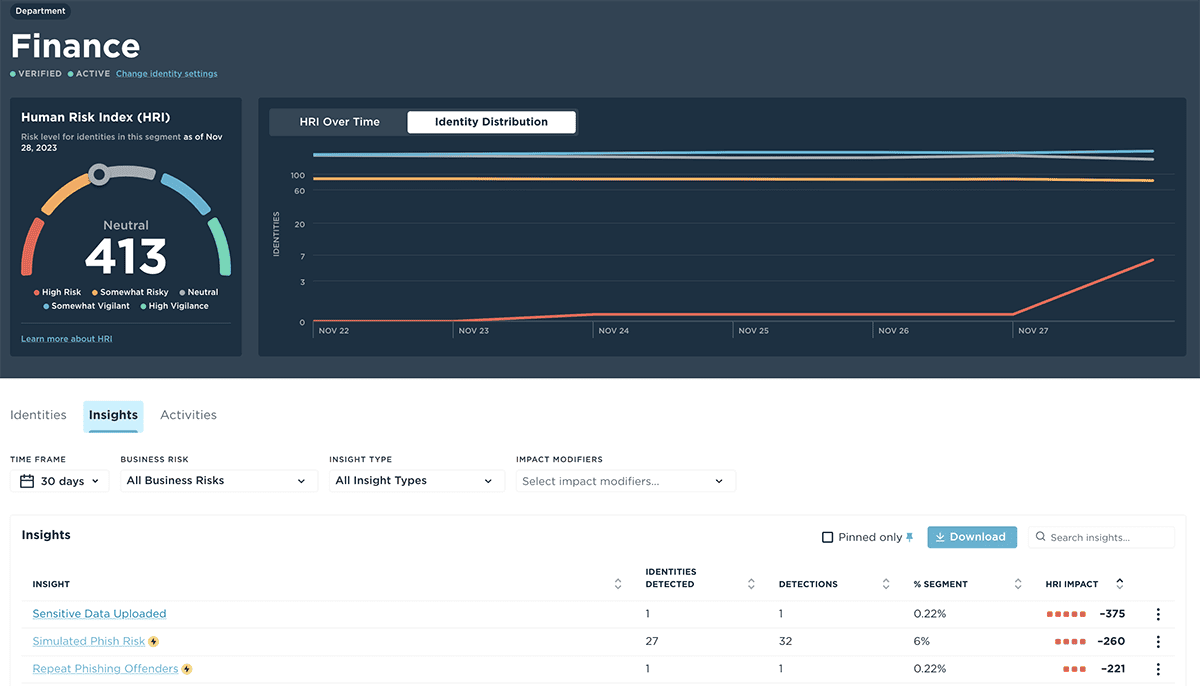
Proactively Protect Your Security Posture
Work smarter with actionable insights that analyze patterns in behaviors to benchmark and identify red flags early and determine prioritization steps.
Gain a deeper understanding of the riskiest and most vigilant individuals and groups within the organization and uncover the activities and context causing risk exposure.
Understand risks, needs, and vigilance by department, individual, location, and role. These insights drive informed decisions across the security program and can trigger targeted action plans to specific risk categories.


In the past, we would look at things like, did people do the online training? As I learned more, I realized that that’s not really enough. It’s really the behavior change that I want. With Unify, I can correlate all our data and in doing so, I learn things that I hadn’t known before.
Brian Markham
CISO at EAB Global
Take a holistic approach
to Human Risk Management
 360 Degree Human Risk Visibility
360 Degree Human Risk Visibility
Expose what others overlook. Correlate identity, behavior, and threat data to reveal who’s really putting you at risk—and why.
See It
 Action on Human Risk at Scale
Action on Human Risk at Scale
Stop risk in its tracks. Trigger targeted action the moment it matters—because risky users aren’t just exposure, they’re your greatest opportunity.
See It
 Always-on Adaptive Defense
Always-on Adaptive Defense
Powered by automation, fueled by intelligence—your defense gets smarter with every human signal. Closing the loop so human risk is everyone’s responsibility—not just IT's.
See It
Feature
Human Risk Management Conference 2024
Human Risk Management conference brings together cybersecurity professionals to discuss improving human risk management and cybersecurity risk management.
Ready to see it in action?
Fortune 500 companies trust Living Security to deliver human risk management by using existing data to identify risky employees or teams and target immersive training to those who need it most. This approach keeps organizations ahead of breaches and enables them to track their progress toward a better security posture. This proactive, automated, efficient approach saves resources while keeping employees and data safe.
Schedule a meeting today and let's get started.

