

PRODUCTS 
Phishing Awareness Training
Stop Phishing Attacks
in their Tracks
Build a human firewall with the most comprehensive solution offering realistic simulations and engaging training, preparing your employees to identify and avoid real-world phishing attempts across all channels.
Empower employees to become cybersecurity heroes.
Don't let phishing attacks reel you in. Living Security empowers you to fight back. Our realistic training simulations, across multiple channels, equip your employees to identify and shut down phishing attempts in their tracks. Respond to email attacks in just minutes, and eliminate the threat from all other inboxes quickly. Living Security integrates seamlessly with your existing security tools, offering a comprehensive and unified defense against the ever-evolving threat of phishing.Why is Phishing, Smishing, and Vishing Simulation Training important?
Cyber attackers want to spread malware or steal data. Social engineering—getting secure, private, or access data from someone in the targeted organization—is how they get in.
Phishing is the attempt to trick someone to disclosing sensitive information via sending a fake email. Smishing is the same practice using SMS messages. When attackers use the phone to trick users into giving up sensitive information, it's called vishing.
Keeping your employees safe, at home and at work, requires testing them by simulating all of these types of tricks across all these channels. Living Security now offers the most comprehensive multi-channel phishing simulation and training ever available.
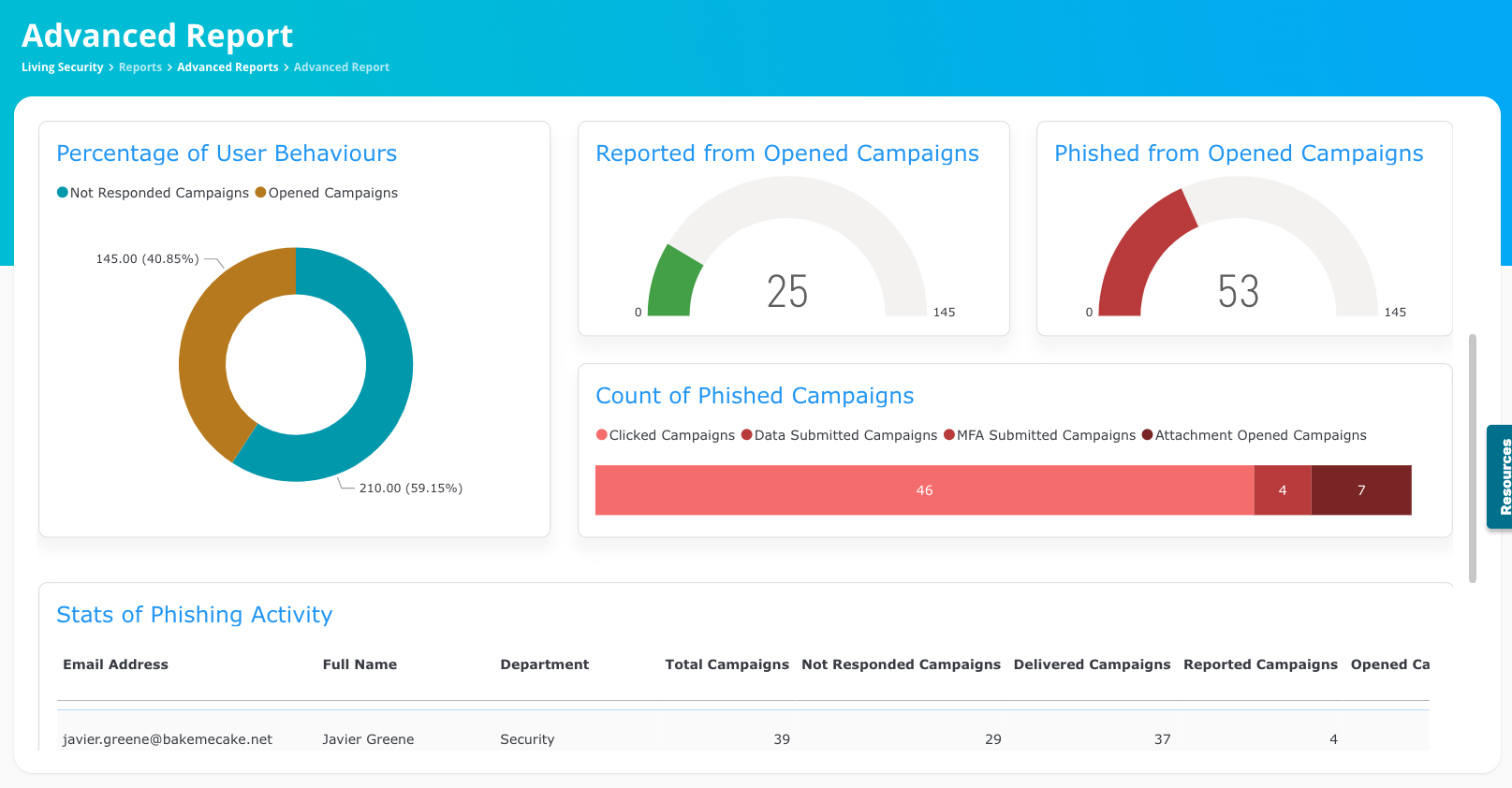
Are phishing simulations effective?
When executed properly, phishing simulation training can be extremely effective. Living Security Phishing, Vishing, and Smishing Simulation offers:
- Always-updated scenario and campaign templates that can be customized for employees based on skill or threat level.
- MFA spoofing, which other vendors don't offer.
- Secure, privacy-focused, realistic simulations available in multiple languages
- Fully AI-enabled, including voice simulation for vishing.
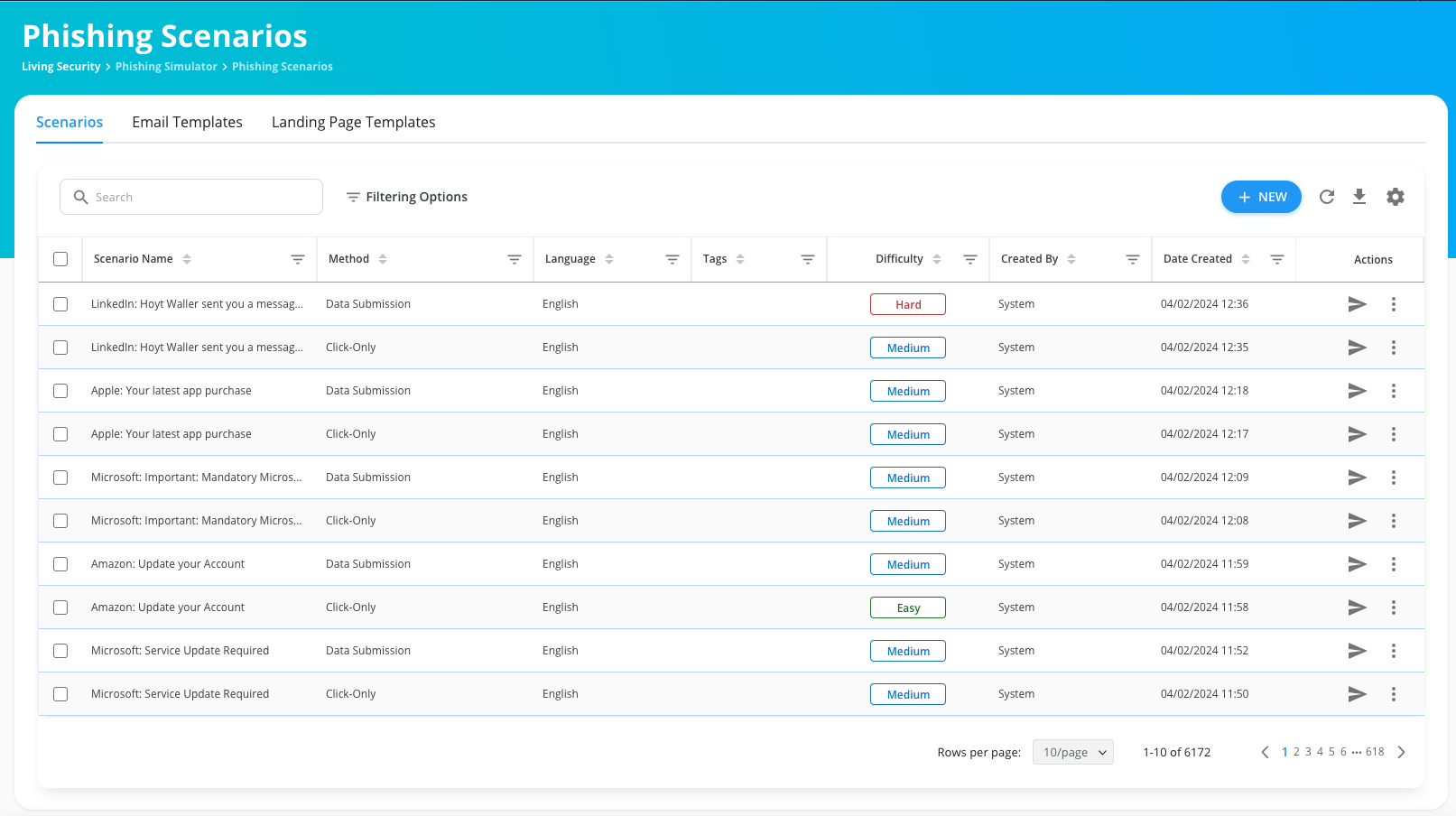
Phishing Simulations
Measure your team’s ability to spot malicious emails with more than 1,600 AI-powered real-world phishing scenarios in over 160 languages.
- Multiple scenarios: Realistic MFA-themed, data submit, attachment, and click-only scenarios that can be customized to test and train employees’ ability to identify and respond to phishing attacks more effectively.
- O365 simulation email: Forget whitelisting, create a simulation email directly in the O365 inbox.
- False clicks begone: Feel confident that your reports won’t include false clicks from security tools.
- Multilingual support: Use custom domains to design phishing scenarios that fit your language and culture.
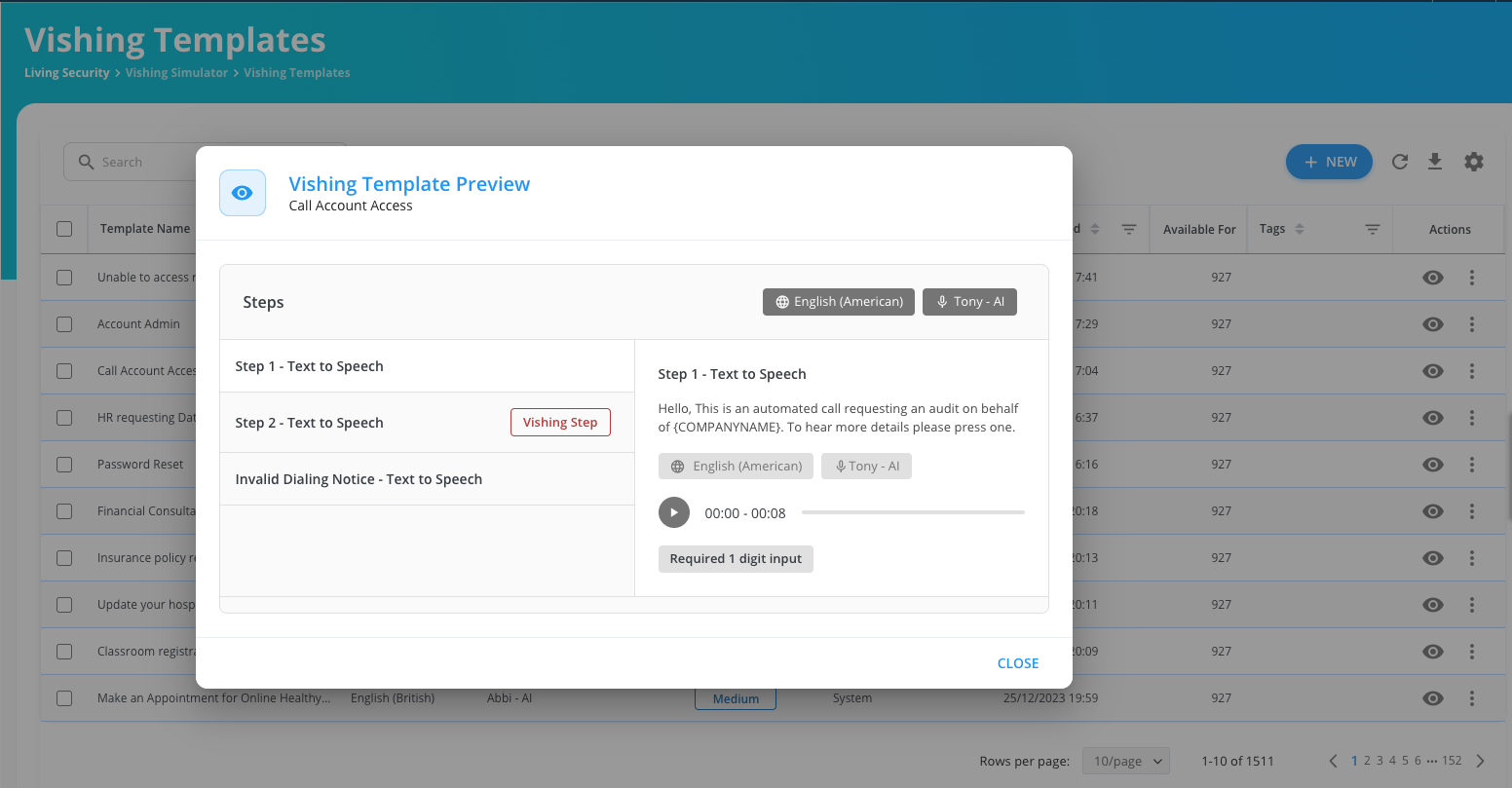
Vishing Simulations
Measure your team’s ability to identify adversaries targeting them over the phone with more than 200 AI-powered and up-to-date vishing scenarios in over 160 languages.
- Scenario customization: Simulate various vishing scenarios based on real-world attacks relevant to your organization, including AI-powered text-to-speech and voice upload.
-Apr-05-2024-04-53-03-6522-AM.png)
Smishing Simulations
Measure your team's ability to recognize attackers using the most up-to-date SMS messages to trick them into providing sensitive information with more than 600 ready-to-use templates in over 50 languages.
- Scenario customization: Customize existing templates or create personalized scenarios relevant to your organization.
- Tailor for proficiency: Individualize campaigns specific to an employees competency.
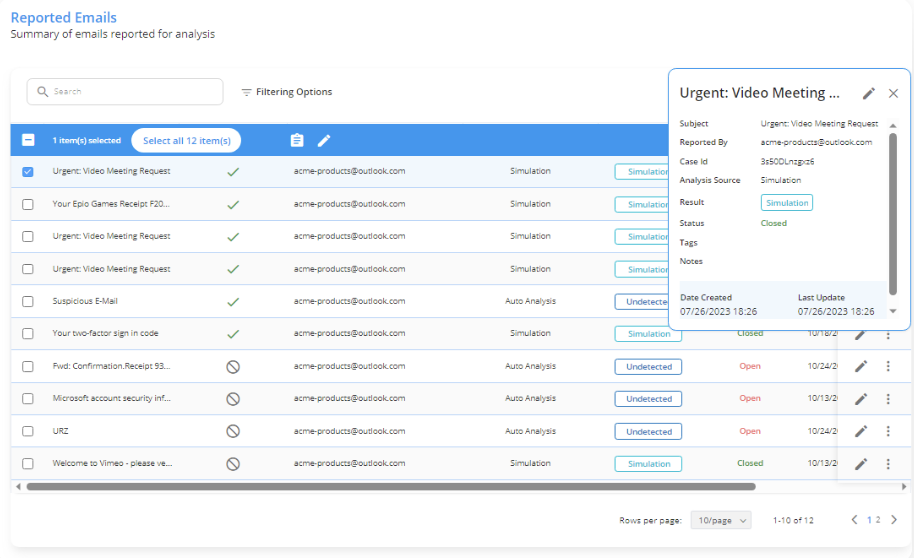
Incident Responder
Identify and remove malicious emails from all inboxes in minutes compared to hours, minimizing potential damage and downtime.
- Foster a vigilant culture: Employees can easily report suspicious emails directly through a user-friendly reporting tool.
- Simplify integrations: Works seamlessly with your existing security tools, avoiding complex setup and ensuring smooth implementation.
- Seamless mail connection: Easily conduct the investigation process through your email server, such as Office 365, Google Workspace, Exchange Online, or On-Prep Exchange EWS.
- Stay ahead of the curve: Leverages AI technology to detect and prevent even the latest "zero-day" attacks, safeguarding your organization from evolving threats.
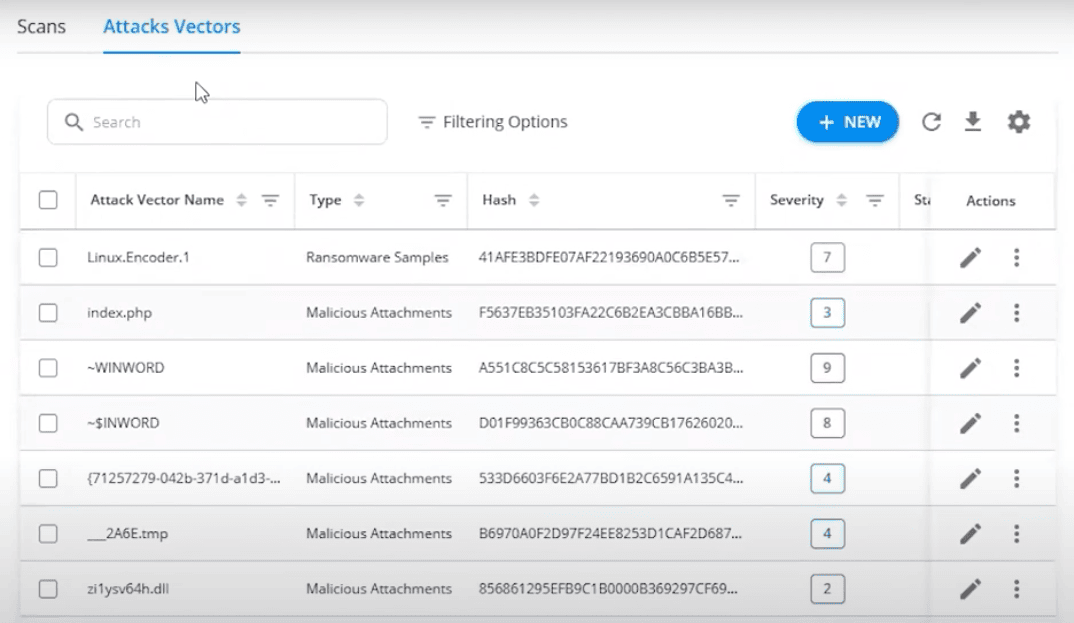
Email Threat Simulator
Send real-world attacks to a dedicated test inbox to identify attacks that bypass SEGs by continuously testing your secure email gateway solutions, including Office 365 and Google Workspace.
- Malicious attachment and ransomware simulation: Test the robustness of your security solutions like antivirus, anti-spam, or sandbox.
- APT attack simulation: Send complex, multi-stage threats often used by advanced persistent threats (APTs).
- File format exploit: Test your vulnerability to different file formats such as PDF, MP4, DOC, M3U, XPL, EXE, and more.
- Client-side attack simulation: Assess your susceptibility by sending phishing emails or malicious downloads that target end-users.
Go beyond awareness with robust features designed to deliver results.
Our robust features go deeper, equipping your employees with the practical skills they need to identify and shut down real-world phishing attempts. From interactive simulations that mimic the latest threats to in-depth reporting that tracks progress, Living Security empowers your team to become a powerful line of defense against evolving cyberattacks.Sharpen cybersecurity instincts: Easily communicate the impact of employees actions on phishing attempts in real-time. This immediate feedback, coupled with relevant training, equips them to become more vigilant and effective against future phishing threats.
Unlock savings: Potentially save up to $200K annually and maximize a return on your investment.
Track progress: Identify areas for improvement with phishing, smishing, and vishing data integrated into Living Security’s Unify to gain insights into employee performance and take action to change employee behavior.
Seamless LMS integration: Fully API-driven platform to automate your tasks.
Continuous improvement: Phishing, smishing, and vishing scenarios are regularly updated to include the latest tactics and techniques of cybercriminals.
Here’s How Living Security Helps You Prevent Phishing Attacks.
Living Security’s phishing simulations and training provide targeted and relevant phishing scenarios and robust reporting to empower your workforce to improve vigilant behaviors.Incident Responder
Email Threat Simulator
Instant Phishing Training Feedback
Integrates with Current Tools
Easy Employee Phishing Reporting
Vishing Simulation
Smishing Simulation
MFA spoofing
Living Security Phishing Modules
We have taken phishing simulation and training to the next level by offering the industry's best solution so you can turn to one vendor for end-to-end Human Risk Management.Living Security’s Email Threat Simulator (ETS) continuously tests your secure email gateway solutions, including Office 365 and Google Workspace, by sending real-world attacks to a dedicated test inbox. Even if you believe you have tight email security, you’ll identify attacks that bypass your SEGs and other vulnerabilities. ETS improves your defenses and helps in the remediation process, optimizing your technological investments.
- Malicious Attachment Simulation: Include real-world malicious email attachments to test the robustness of your security solutions like antivirus, anti-spam, or sandbox.
- Ransomware Simulation: Test the secure email gateway and associated security solutions using known ransomware attacks.
- APT Attack Simulation: Test your email security by sending complex, multi-stage threats often used by advanced persistent threats (APTs).
- File Format Exploit: Test your vulnerabilities associated with various file formats like PDF, MP4, DOC, M3U, XPL, EXE, and more.
- Client-Side Attacks Simulation: Assess your susceptibility by sending phishing emails or malicious downloads that target end-users.
- Customized Testing: Add your malicious attack vector to the platform and test your email gateway, data loss prevention (DLP), Sandbox, and all similar security products in your network.
- Seamless Email Testing with Outlook Web Access: Integrate with Outlook Web Access or O365 for email security testing if you have restricted services like POP3/IMAP.
- Detailed Reporting: Receive comprehensive reports with suggestions on the vulnerabilities to quickly fix them and get a company score on your email defense capability and boost it. Fully integrates with Living Security Unify.
- Automated Scanning and Continuous Defense Checks: Automatically scan your email gateway tools with newly added attack vectors to maintain your security at all times.
On average, it takes 9 hours to detect and remove a malicious email, significantly amplifying the risk. But Living Security’s automated phishing incident response tool helps you identify and respond to email attacks in approximately two minutes.
Then it removes the threat from all other email addresses immediately.
- Find and remove suspicious emails from your inboxes in minutes. For example, a scan and removal from 7500 inboxes took just five minutes.
- Works with your existing email security tools, analysis engines, SOAR, and other platforms, including Living Security Unify.
- Available on-prem or via the cloud.
- Phishing Reporter lets employees easily and immediately report phishing emails directly from their inbox to Incident Responder.
- Streamlined Processes: Create customizable rules for efficient classification of reported emails.
- Seamless Mail Integration: Easily conduct the investigation process through your email server, such as Office 365, Google Workspace, Exchange Online, or On-Prem Exchange EWS.
- AI Support: Leverage AI capabilities to detect and prevent zero-day attacks.
Living Security Phishing Simulator allows you to gauge your security culture with AI-powered 1600+ ready-to-test phishing scenarios in 160+ languages and trains your employees to identify and respond to these attacks.
- No Whitelisting required for O365: Our phishing simulator creates a simulation email directly in the inbox
- Multiple Scenarios: Realistic MFA-themed, data submit, attachment, and click-only scenarios to test and train employees' ability to identify and respond to actual phishing attacks.
- Automatic elimination of malware: No false clicks on reporting as we automatically detect and eliminate automated security tools clicks on simulated phishing campaigns!
- Customizable templates to simulate a variety of phishing attacks.
- Automated reporting for detailed information on employee performance. Fully integrates with Living Security’s Unify to easily identify vigilant users.
- Multilingual support for international organizationsContinuous improvement to keep up with the latest phishing tactics and techniques.
- Freedom to use custom domains to design phishing scenarios that fit your language and culture.
- SSL-enabled phishing domains in your phishing scenarios that make your campaign realistic and secure while you’re improving your security culture.
- Fully API-driven platform to automate your tasks and integration with any LMS
- Multiple phishing scenarios randomly delivered to your employees to improve individual security culture.
If you have a customer support phone number, you need vishing simulation. Living Security Vishing Simulator delivers 200+ AI-powered ready-to-test vishing simulations in 160+ languages to train your employees to recognize and respond to these attacks.
- Scenario Customization: Simulate various vishing scenarios, including AI-powered text-to-speech and voice upload.
- Realistic Scenarios based on real-world attacks relevant to your organization.
- Automated Reporting: Fully integrates with Living Security Unify for Human Risk Management.
- Continuous Updates: Ensures your training remains updated with the latest vishing techniques.
- Global: Multilingual support for global organizations.
- LMS Integration: The most comprehensive API-driven integration available across your platforms.
In smishing, attackers use SMS messages to trick recipients into providing sensitive information. Using over 600+ ready-to-use templates in 50+ languages or customizing your own, you can quickly identify the weakness within your organization and fix the problem.
- Scenario Customization: Customize existing or create personalized scenarios.
- Comprehensive Library: Access a constantly updated collection of over 600+ smishing scenarios to simulate real-world SMS attacks.
- Continuous Updates: New scenarios are added regularly, ensuring your training remains updated with the latest smishing techniques.
- Real-time reporting, fully integrated with Living Security Unify: Gain insights into employee behavior and performance with automated real-time reporting, allowing you to track progress and identify areas for improvement.
- Multilingual Support: Cater to the needs of global organizations with multilingual support, providing training materials in multiple languages.
- LMS Integration: The most comprehensive API-driven integration available across your platforms.
- Varied Difficulty Levels: Tailor the experience based on your employees' proficiency levels

Feature
Human Risk Management Conference 2024
Human Risk Management conference brings together cybersecurity professionals to discuss improving human risk management and cybersecurity risk management.
Ready to see it in action?
Fortune 500 companies trust Living Security to deliver human risk management by using existing data to identify risky employees or teams and target immersive training to those who need it most. This approach keeps organizations ahead of breaches and enables them to track their progress toward a better security posture. This proactive, automated, efficient approach saves resources while keeping employees and data safe.
Schedule a meeting today and let's get started.

