
Explore HRMCon
On-Demand
Dive into the insights and discussions from HRMCon. Watch the recorded sessions at your convenience.
Each year, HRMCon brings together cybersecurity thought leaders and practitioners to present a half-day virtual conference geared toward continuously evolving the power of behavior change in mitigating risks.
.png)
.png)
HRM 
Explore HRMCon
On-Demand
Dive into the insights and discussions from HRMCon.
Each year Human Risk Management Conference brings together cybersecurity risk management thought leaders and practitioners to present a virtual conference geared towards continuously evolving the power of behavior change in mitigating human risks.




















TITLE
TITLE
TITLE
TITLE
Breakout Tracks |
|||
Human RiskQuantification |
Risk-BasedPolicy & Training Interventions |
Workforce Educationand Enablement |
PositiveSecurity Culture |
Quantifying Behaviors to Mitigate Human Risk in HRMChris Poirel, Living Security |
Targeting Awareness of Cyber Threats with Risk-Based Policies & Training InterventionsDavid Tunley, Rivian |
Hook, Line, and SinkerAaron Strong, Syniverse |
Building a Robust Security CultureTerry Smith, Blackbaud |
|
|||
Human Risk Management 2.0Jon Brickey, Mastercard |
Empowring Your Human Firewall: Orchestration for Cyber Resilience and TrainingSandy Evancs, Living Security |
How to Deepen Your Career in Security AwarenessCassie Clark, Consultant |
HRM's Role Cultivating a Positive Security Culture for your OrganizationShawnee Delaney, Vaillance Group |
|
|||
The State of Human Risk QuantificationMaria Long, Violet Sullivan & Julian Sylvestro |
MindSecure: Elevating Cyber Resilience through Cyberpsychology and Organization SynergyAllen Ohanian, LA County |
Own Your Security Journey: Empower All Levels to Track Human Risk & Drive Continuous ImprovementErik Book, Living Security |
Borrowing Brilliance: What Security Awareness and Training Should Steal from MarketingMike Taylor, Nationwide |
Connecting Emerging Threat Intel to Human Risk QuantificationJosh Bartolomie, Cofense |
Evolving from Annual Security Compliance Training to Risk-Based Policy and TrainingMichele Kim, Fitch Ratings |
Using Human Risk Management to Drive Behavioral ChangeBrandy Harris, CyberEd |
Scorecards & Vigilance: Unleashing the Power of Your Workforce for a More Secure FutureNick Marchiselli, Living Security |
Conference Tracks
Choose from four exciting conference tracks.1. Human Risk Quantification
2. Risk-Based Policy & Training Interventions
3. Workforce Education and Enablement
4. Positive Security Culture


The Future Is Now: Introducing Human Risk Management. This is not just a name change. It is a significant change of mindset, strategy, process, and technology about how we approach an old problem in a new world.
Jinan Budge
Keynote Speakers
Review extended insights into human risk management from renowned thought leaders in the cybersecurity risk management industry.
David Kennedy | TrustedSec
David Kennedy, founder and CEO of TrustedSec, and subject matter expert in cybersecurity presents Unveiling the Adversary: War Stories & Discoveries from the Human Element. During this keynote hear war stories and discoveries of advanced attacks including voice cloning and ransomware attacks. Dive into how businesses can prepare for these advanced scams and attacks through human risk management. WATCH SESSION
Jess Burn | Forrester
Jess Burn, principal analyst at Forrester specializing in incident response, crisis management, and email security, presents The Future is Now: Introducing Human Risk Management. This session examines the major expected changes in SA&T as the cybersecurity risk management industry transitions to an approach that centers on behavior, prioritizing positively influencing behavior and instilling a security culture within organizations.
WATCH SESSION
Brian Krebs | KrebsOnSecurity.com
Decorated independent investigative reporter, Brian Krebs, joins Living Security CEO, Ashley Rose, for a Fireside Chat: What Breaches Teach Us. From data spills, breaches and thefts, to breach fatigue, apathy and cynicism, this discussion will examine some of the more alarming trends in cybercrime, and offer perspectives on how businesses can up their cybersecurity risk management game in response.
WATCH SESSIONWatch Breakout Tracks
Detect and measure human security behaviors by identifying vigilant and vulnerable members of your workforce. Use data from your existing identity and security tools to quantify human risk across the full spectrum of security risks including account compromise, data loss, malware, phishing, social engineering, and training compliance.
Initiate policy and training interventions based upon human risk. Interventions should be based on best practices and provide next steps that can be taken in real-time to address risk such as nudges, reminders, microlearning modules, and policy changes.
Educate and enable the workforce to protect against cybersecurity risks. Empower individual employees, managers, and executives to measure progress and track vigilance across teams and departments.
Build a positive security culture by empowering your workforce to actively participate in security vigilance, eliminate needless compliance activity, and incorporate intelligent capabilities that simplify security compliance.


The Future Is Now: Introducing Human Risk Management. This is not just a name change. It is a significant change of mindset, strategy, process, and technology about how we approach an old problem in a new world
Jinan Budge


Browse Curated Collections


Book a Demo

More from Living Security
HRM Ask Me Anything
A monthly series bringing together the industry's top experts focusing on a variety of cybersecurity and human risk management topics.

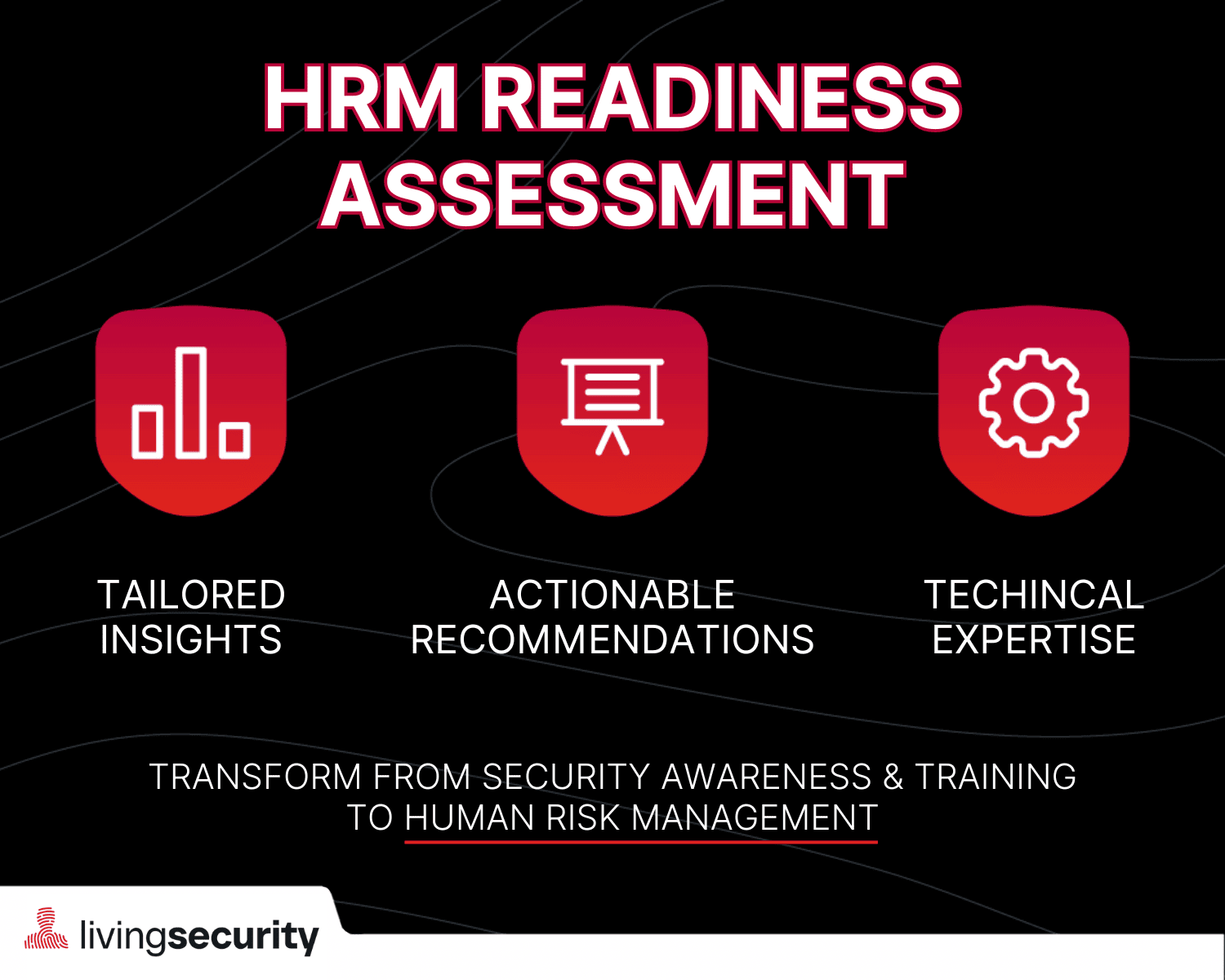
Readiness Assessment
Living Security’s experts assess your organizations readiness to transition to comprehensive human risk management.
Schedule a Demo
See how your organization can easily identify groups with similar risks and protect with nudges, training, and policy updates.









































