

Blogs 
May 19, 2020

Graham Westbrook
Verizon DBIR 2020: A Feast for Security Awareness

Smell that? Ya. It's a whiff of the fresh, new Verizon Data Breach Investigations Report (DBIR) hot off the press. This is usually the time when CISOs, SOC analysts and security awareness program owners all huddle in the corner of the office and pore over the results, ooing and aahing about bar charts and trend-lines. These days, I guess we'll have to settle for nerd moments in quarantine.
I know what you came here for, so I'll give you what you want: there are some RICH insights here for security awareness. And no, I don't want to just treat you to a special edition of awareness-flavored confirmation bias. I want us both to have a pinky's-up, 5-course meal in security awareness, where we don't just chew the meat and spit out the bone. Get your bibs out, team, and prepare to feast...
First Course: Starters
- Security "awareness" was called out 14 times.
- 12 of those 14 call-outs were recommending that organizations "implement a security awareness and training program," like... yesterday. (RE:Center for Internet Security's CSC #17).
- Security "awareness" was listed as a top control for 80% of industries listed. Meaning, the vast majority of all industries got an explicit call-out in a TOP-FOUR recommendation for security awareness. The only industries that didn't get an explicit call-out were Accommodation & Food services, Construction & Retail...
- 67% of breaches were caused by credential theft, errors and social attacks... a.k.a. facilitated by the human. We all know how to read between the lines, here, and it requires commitment and consistency to train the human operating system. As we'll see soon, there are some good things happening that are directly related to security awareness efforts.
Second Course: Healthy Stuff
- Phish click rates are "as low as they ever have been" (3.4%), and phish reporting rates are "rising, albeit slowly." This is HUGE, team. Phish reporting numbers are now hovering around ~40%, up from 20% in 2016. That is AMAZING and all thanks to YOU.
- Misuse ("intentional actions undertaken by internal employees that result in some form of security incident") is trending down as a percentage of incidents. (*Verizon notes that could be attributed to lower granularity data this year and may rise back to previous levels in 2021. On the other hand, breaches are showing a legitimate drop, which appears to be associated with less misuse of databases to access and compromise data).
- "No relationship" between credential leaks and credential stuffing, the week following a breach. Apparently, cyber criminals merely gobble up the new breaches whenever they update their credential stuffing dictionaries.
Third Course: Tasty Facts
- 86% of breaches in 2019 were financially motivated... Cyber criminality, it seems, is not just for the 'lulz'
- 30% of breaches involved internal actors (almost 1 in every 3 breaches)... while, 70% involved outsiders (* as you might expect, because there are more people outside than inside an organization). Still, with some estimates that only 1 in 10 insiders get caught, there may be a significant 'dark number' here that is not yet reported. Obviously, the DBIR is a trailing indicator and cannot account for things yet unreported, so take it with a grain of salt.
- ~60% of breaches were perpetrated by organized crime groups (the rest a smattering of nation-state, end users and sys admins). This is a big revelation for some, because sometimes attribution is a proxy for risk. Meaning if you know WHO you're dealing with, you often know HOW to fight back against their known capabilities.
- >80% of breaches (within "hacking" incidents) involve Brute force or the Use of lost or stolen credentials. Again, this has a mega human factor, in that people are on the hook to protect their credentials and report suspected compromise. The good news is that people can be trained!
Fourth Course: Main Courses
- Phishing remains top threat "action" among threat actors. A good reminder to reinforce our phish education programs and keep up the friendly phishing through 2020!
- Threat actors went after email addresses, credentials and changed user behavior in that order. Verizon considers these the "top compromised attributes" across industries. If we're doing defense-in-depth, lets start with these prized assets and work our way outward!
- Human exploit attempts (known as "social actions" in DBIR) arrived via email 96% of the time, while 3% arrived through a website. A little over 1% were associated with Phone or SMS, which is lower than expected. A good reminder to not pivot too hard to smishing topics, but hang on to tried-and-true phishing education.
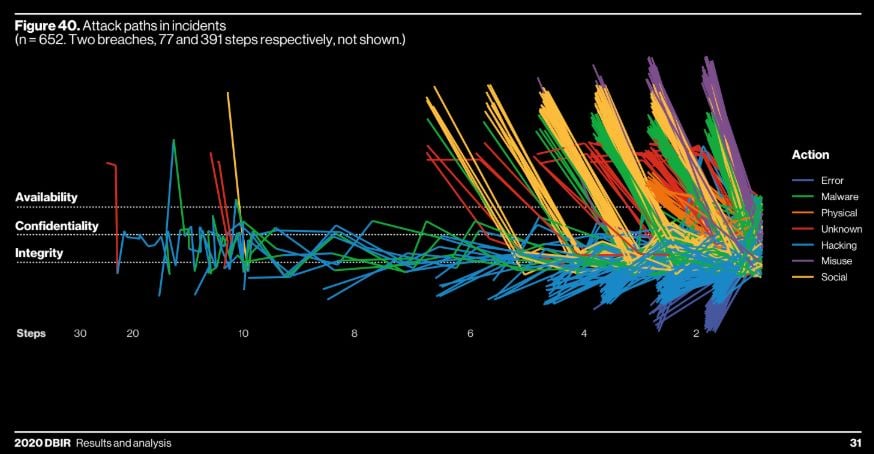
- Attackers prefer "short paths and rarely attempt long paths." Below, Figure 40 is basically just a pretty illustration of the trend of cyber criminals finding the quickest and easiest route to their victims. Read it left-to-right, and see how few attack journeys start at left. This means threat actors are LAZY and that they STILL take the path of least resistance. Don't give them more low-hanging fruit!! Add an obstacle. If there ever was a case for 2FA...
Fifth Course: Unhealthy Stuff
- The only action type that is consistently increasing year- to-year in frequency is Error. People make mistakes, but this is one to watch out for! (*"The fact that we now see Error becoming more apparent in other industries could mean we are getting better at admitting our mistakes rather than trying to simply sweep them under the rug.")
- Financially motivated social engineering (FMSE) is on the rise. In Appendix C of the DBIR, two members of the US Secret Service, Michael D'Ambrosio (assistant director) and Jonah Force Hill (Sr. cyber policy advisor) take a stab at analyzing the overwhelming number of hacking incidents that are financially motivated, and end with a plea to "work together" to protect and defend networks and create choke-points for criminals to be caught, arrested and prosecuted. (*In 2019, the Secret Service prevented $7.1 billion of cybercrime losses and returned over $31 million in stolen assets to victims of fraud.")
Mmm. I needed that. High-calorie feast on security awareness facts that gives us sustenance for the task ahead: move the needle on behavior change, culture change and helping organizations win!