

Blogs 
September 11, 2019

Graham Westbrook
Cyber Threats - The 7 Deadly Sins of Security Awareness - a Living Security Intelligence Report

Cyber Threats
7 cybersecurity ‘sins’ are responsible for the majority of your human risk.
Meaning, employees who are unaware of (or intentionally) committing these seven security blunders are significantly more likely to assist or accelerate cyber attack against your company:
- Misinterpret legitimacy
- React impulsively
- Over-rely on security controls
- Disregard policy
- Mishandle devices
- Neglect suspicious activity
- Surrender to security fatigue
The cost of ignoring these ‘sins’ is steep. A successful cyber attack in 2019 is over $5 million USD on average, or around $301 per employee (ponemon). Coupled with the fact that people are now 20x more likely to be robbed at their computers by a cyber criminal than to be held up in the street, the urgency becomes all the more real for people to become situationally aware of current and emerging threats before it's too late.
Traditionally, the reaction by security awareness program owners has been some form of blame-and-train. But better program design means taking responsibility for any resistance and instead choosing to influence culture change through non-punitive action steps. Sustaining culture change requires understanding not just behavior, but also the identity and motivation behind each decision made.
The Sins
-
Misinterpreting email legitimacy
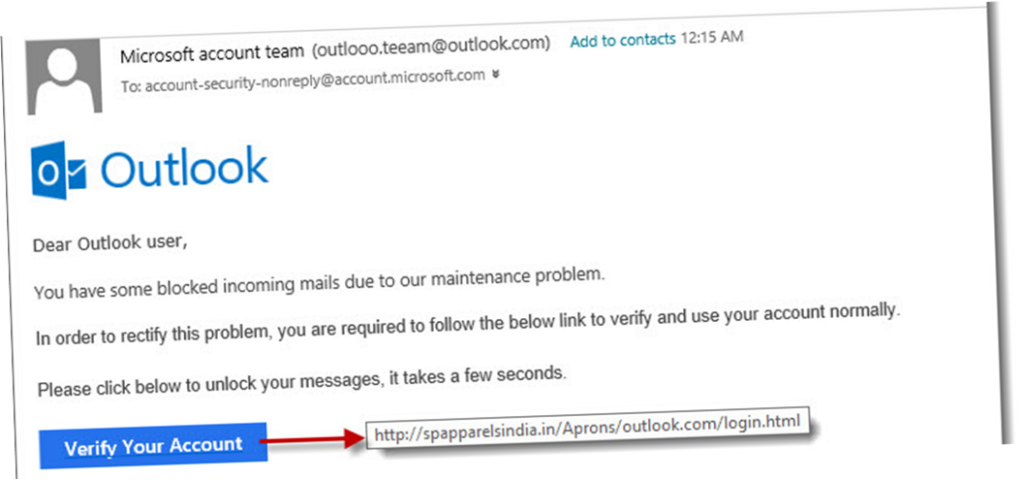
- 91% of cyberattacks begin with a phishing email (TrendMicro)
- 86% of people said they had received more than one suspicious email in the last two weeks, and a majority of them said they would appreciate additional training (Living Security)
- 76% of businesses reported being a victim of a phishing attack in the last year. (Wombat Security)
- 56% of organizations identified targeted phishing attacks as their biggest current cybersecurity threat. (CyberArk)
- 30% of all phishing emails are opened, 12% clicked (Verizon)
-
Reacting impulsively to suspicious calls

- Being “caught off guard” and “curious” were the two main reasons why respondents fell for social engineering scams, according to a Living Security study. For respondents being “caught off guard,” they did not understand that it was OK to hang up, collect their thoughts, talk to security and call back (if applicable). “Curious” respondents, on the other hand, were unaware of the dangers of inquisitiveness.
-
Over-reliance on mobile security controls

- Millions of people have over-trusted the native security controls of their phone. The obvious corporate implication is that users will inevitably bring compromised devices into the workplace (barring strict BYOD policies) and connect to WiFi (NetworkWorld). Moreover, the next wave of malicious mobile applications is expected to be even more advanced, with botnet tendencies to actually hijack and control infected devices (VeraCode).
- 73% of people admit to not notifying IT when their device has been infected (webroot)
-
Disregarding policy guidelines

- Policy questions had the lowest net score on the Living Security platform in 2018, indicating a difficulty identifying appropriate responses to corporate policies and industry regulations.
- 12% of employed respondents were fully aware of the IT security policies and rules set out by their employers (B2B International, Kaspersky Lab)
-
Mishandling company devices while teleworking or traveling

- 64% of people felt their role made them a moderate to high risk target for cyber criminals, many without an adequate understanding of what security precautions to follow while teleworking or traveling. This attack surface presents a significant risk for accidental loss, theft or tampering of company-furnished devices while away from the workplace. (Living Security)
-
Neglecting to challenge strangers on premise/ reporting suspicious activity on network

- 90% of all cyber crimes stem from minor oversights (on premise or on network), whether because of gross neglect or stress. (Willis Towers Watson)
-
Surrendering to password fatigue

- Password-related questions are one of the most misunderstood topics among end users on the Living Security platform, and some indicate the practice of reusing passwords across all their platforms, or merely incrementing/decrementing them to only slightly change the base password (Living Security). Recent reports show that users are also overwhelmed with managing an array of passwords and are looking for “convenience” (Yubico -Ponemon study).